Have you had a year free of cybersecurity events, and assumed that meant your business was never targeted? There’s a lot that goes on behind the scenes in IT security to ensure attack attempts never lead to an incident that compromises your business.
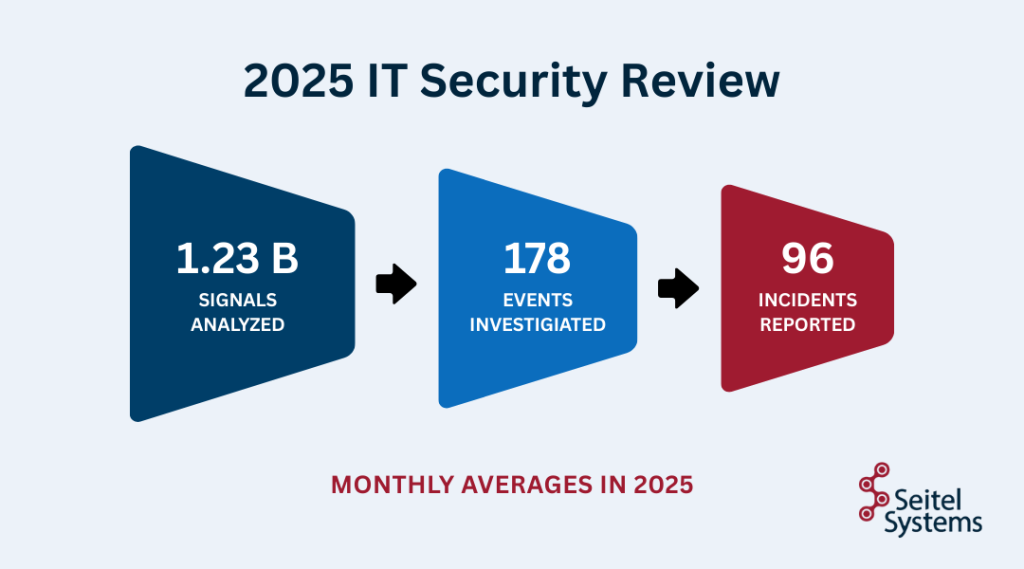
Table of Contents
This year, an average of 1.23 billion events a month from our clients were monitored for suspicious activity. Of those events, an average of 178 suspicious signals were manually investigated by a security analyst after automated analysis. An average of 96 incidents a month were reported and addressed.
What were those incidents? We did a review of the most common types of cyber attack attempts that we saw this past year while protecting our clients, and here’s what we found. We will break down the most common types of attack attempts from 2025, along with the best security measures you can put in place to protect against them:
2025’s Top Cybersecurity Threats
This year, various types of social engineering attacks were the most common threat. In a social engineering attack, “an attacker uses human interaction (social skills) to obtain or compromise information,” according to the Cybersecurity & Infrastructure Security Agency. Below are the attacks that, month over month, remained common threats and were sometimes used in tandem.
Cloud Account Takeovers (ATO)
This year, one of the primary threats observed was cloud account takeovers (ATOs), often indicated by anomalies like unusual email logins. These ATOs occur when attackers successfully obtain user credentials or tokens through various techniques. The most effective defense continues to be a combination of user education, which empowers them to act as a “human firewall,” and robust technical safeguards.
Many of the attacks against cloud identity accounts came from internet service providers (ISPs) with malicious autonomous system number (ASN) ratings (a rating that determines the probability of malicious activity originating from that network). By launching attacks from ISPs with these overly lenient policies, threat actors are using time-tested techniques. Some of these included sending Business Email Compromise (BEC) emails or manipulating a user’s inbox with rules to redirect or hide messages. Adding security “speed bumps” like MFA and providing awareness training are great ways to slow down threat actors and help protect user identities.
Adversary-in-the-Middle (AITM)
One of the reasons cloud ATOs persist is because of proven tactics like Adversary-in-the-Middle (AiTM). This year saw a surge in attacker-in-the-middle (AiTM) attacks, where adversaries intercept credentials and MFA codes using fake login pages. After the initial compromise, attackers gained access to identities and inboxes, which led to account takeovers, data theft, and even payment redirection. Combat this threat with conditional access policies and user training. Security awareness remains key: educating employees to spot and report deceptive login prompts is essential.
Remote Management and Monitoring (RMM)
One of the other most common social engineering attacks this year involved remote management and monitoring (RMM) tools. Attackers use deceptive names like “client,” “statement,” “invoice,” or “social security” in phishing lures to download malicious RMM tools. We also saw an uptick in seemingly harmless files being renamed as Remote Monitoring and Management tools to gain access to endpoints. After establishing access, the threat actor would establish persistence next and then immediately start moving laterally. Using strong two-factor authentication mechanisms, along with keeping basic security hygiene in place (like turning on logging), goes a long way towards defending against attacks like these. Beyond technical solutions, a strong defense continues to be training end-users to report suspicious activity.
Other Notable Cybersecurity Threats This Year
These threats surged early in the year, but they didn’t remain a top threat throughout the rest of 2025:
ScreenConnect
Early in 2025, the top threat involved a type of RMM tool attack, with users being tricked into downloading and executing malicious ScreenConnect instances, granting attackers remote access to compromised systems. The primary vector involves luring targets through phishing emails or fraudulent support calls. The recommended mitigation is robust security awareness training, empowering users to recognize and avoid such tactics, coupled with strict endpoint monitoring and application control policies.
Lumma Stealer Malware
In February 2025, we saw a rise in Lumma Stealer (an infostealer malware) infections, often spread through fake CAPTCHA prompts on malicious ads and compromised sites. Users are tricked into downloading disguised malware, leading to credential theft, session hijacking, and crypto wallet compromise. To stop it, enforce endpoint security, block suspicious downloads, enable MFA, and educate users on spotting fake CAPTCHAs. A proactive defence would also be to disable the Windows Run prompt via Group Policy.
How We Protected Your Team and Network
We partner with the industry-leading security provider Huntress to provide our clients with 24/7 security monitoring. They use the best of technology and human intelligence working together to monitor for and protect against security threats.
From our review, you can see that many attacks come through social engineering and steal target accounts or login credentials. This is why we emphasize the importance of employee security training for awareness and tools like MFA to slow down and prevent attacks even when login credentials are compromised.
If you need to put protections in place for attacks like the ones mentioned above, our experts work to put multi-layered security in place that covers the recommendations above, including network protections, user account security, employee training, and 24/7 monitoring to respond if an attack attempt does occur. Do you have any questions or concerns about these security threats? Feel free to reach out for a conversation!

